Security, Privacy Are Lost Causes … Get Over It

All around the globe the privacy, security conundrum is a mell of a hess!
You have 60 to 90-year-old regulators establishing rules/laws for 30 to 50-year-old executives/ engineers to follow in developing products and services that 20 to 40-year-olds want to use that 10 to 20-year-olds can crack for the hell of it or for profit.
Talk about generation gaps!
In the U.S., we have everyone in Congress and a bunch of agencies wanting to write the laws.
Every country wants its citizens’ content private (not mined); but they also want – nay demand – the server owners make stuff available when they want it … better yet, give ‘em the source code.
They’ll do the rest.
Of course, only a freakin’ idiot would give up the company’s crown jewels–even if the folks criss-crossed their heart and promised not to misplace them.
Cisco was a little more blunt about such requests and told ZDNet, “We have not and we will not hand over source code to any customers, especially governments.”
Government agents here and abroad interpreted that for their bosses … well, maybe.
In a number of countries (no one knows how many), law enforcement and intelligence agencies find zero day vulnerabilities (they’re bad, trust me), but don’t tell software folks or you/me about them because “they may need them” to search someone’s devices or files.
Ignore that each government works to find out what’s going on in the other government. You and I don’t care about them … it’s all about our company, our personal stuff!
It’s all okay … as long as you don’t think about it too much.
 The Internet infrastructure is old and has patches on top of patches, just like the well-traveled streets and roads in your town.
The Internet infrastructure is old and has patches on top of patches, just like the well-traveled streets and roads in your town.
We’ve already gotten off to a very profitable breach start for 2016 with the announcement that 272.3 million stolen accounts were “liberated” in Russia and an unknown number from Google, Yahoo, Microsoft and services around the globe.
Perhaps as many as 1.2 billion records have been purloined on top of a growing number of electronic bank heists.
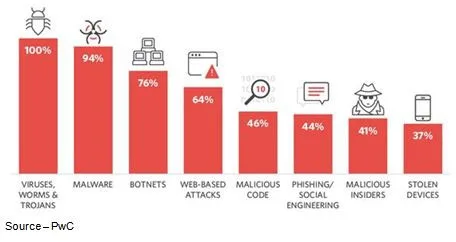
Cisco’s recent security report noted that companies and individuals have seen a major increase in security threats:
- Malware – 54 percent
- Ransomware – 53 percent
- Phishing – 46 percent
- Data leaks/theft – 39 percent
- Spyware – 38 percent
- Password breach – 37 percent
Nearly 90 percent of attacks involve financial or espionage motivations.
The top 10 known vulnerabilities account for 85 percent of successful exploits.
Ransomware attacks were up by 16 percent worldwide last year, according to Verizon’s report.
All thanks to the growing number of devices used and POEs (points of entry):
- Laptops – 81 percent
- Desktops – 73 percent
- Smartphones – 70 percent
- Tablets – 62 percent
- 30-40 B Things
Cisco has reported that 95 percent of the devices we use to communicate with at the office – BYOD (bring your own device) – have known issues since security wasn’t one of the big customer features most firms designed into their devices when the offered them to you.
But the other weak points are:
- Servers – 49 percent
- IoT devices – 49 percent
- Wireless access points – 47 percent
- Routers and switches – 38 percent
As a result, most corporate managers are increasingly concerned about their vulnerability because there are major compatibility issues between the various technologies.

While you might expect SMBs (small-medium businesses) to be the most vulnerable, they actually do better with their security.
Increasingly, the firms outsource their protection to security services that focus 100 percent of their attention on auditing, monitoring, incident response/resolution, data mining, etc.
Courtney Bowman, a member of the privacy and civil liberties group at Palantir Technologies, notes that information security is a key component of privacy and emphasizes that information must be held securely.
But Verizon’s recent global security report emphasized that there’s no such thing as an impenetrable system. They found, however, that if basic defenses are used; hackers, whackers and cybercriminals will simply move on to find an easier sucker/target.
Forget about the slick attacks you see in the movies, most of the hacks/breaches could be easily prevented:
- Non-existent security implementation at the beginning of a product’s/service’s design
- Two-thirds are because of weak, default or appropriated passwords.
- 85 percent are achieved by taking advantage of known and unpatched problems everyone has known about for months, years.
- The majority are caused by people inside the organization who ignore protocols or unwittingly open the door for a breach.
Phishing is the most popular approach to penetrating a corporate network or individual’s device.

You know, that Nigerian prince, dying wife of a bigwig, person who was mugged somewhere, lawyer who wants to give you a $5M (more/less) inheritance because your name sorta’/kinda’ sounds like, your boss requests a couple of hundred grand sent to someone, a zipped invoice, and the fantastic “I can’t believe how rich I’m going to make you” proposition.
Verizon reported that 30 percent of phishing messages were opened and nearly 15 percent actually clicked on the infected attachment or link included.
The newest wrinkle is fake social media sites that are even more profitable than the phony banks.
Now I’m a glass half-full guy, except when I go online. If I think twice about it … it’s in the trash!
These folks are out to steal your data because of what it’s worth, not who you are.
Anything that can be converted to money will do.
I’m not as bad as Palantir’s Bowman who doesn’t engage in social media, but I do limit my online presence.
Like you, I don’t read the cockroach dung-size type in the terms of service; however, I do turn off my device tracking … just in case.
Big Dark Web exploits get all the news coverage but the real culprit is marketing … lifestyle marketing.
There’s a constant barrage of tailored ads and personalized messages that you actually sign up for!
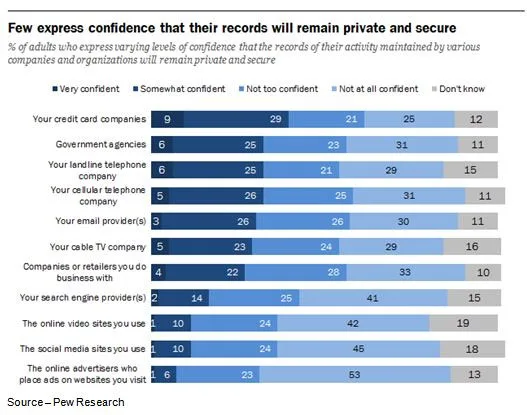
You wanted the special deals, exclusive offers, club status, you name it.
That’s not “so” bad; but for the most part, all they’re interested in doing is gathering the data and mining it for their use.
Protecting it? Not so much!
So over the long run, it’s more insidious than a hack.
 However, I agree with Jon Osterman, “Without condoning … or condemning. I understand.”
However, I agree with Jon Osterman, “Without condoning … or condemning. I understand.”
# # #