People Can’t Pass Off the Responsibility of their Cybersecurity

Forget the fact that corporate executives and government officials are in an uproar about the reported computer hardware supply chain hack.
You can’t do anything about it.
Right now, it’s just the storyline for a great sci-fi movie.
Besides, you’re more concerned about your stuff that’s being spread around the Web.
You already don’t trust Facebook with your personal data. You don’t trust Twitter with your personal data. You don’t trust Instagram with your personal data.
Heck, you don’t even trust your bank; your national, regional, local government; your local retailers, your online stores, your healthcare service providers; and probably not even your own company.
Why?
Some organizations simply sell your info to others who want to sell you stuff/ideas.
Others want to use it to do a better job of meeting your needs.
A few just like to have a bigger data pile than the next guy.
And yes, some use your data for “other” purposes.
It’s become such a daily occurrence that government officials want to establish a “national standard for privacy rules,” which sounds great.
However, a recent Pew Research report noted that for a $3 cup of coffee or a couple of added coupons/discounts, you’ll give people all of the information they want.
Thank you very much!
Most organizations will do their darndest to keep their (and your) data from prying eyes; but it’s sorta’, kinda’ a losing battle for them.
In fact, cybercrime reports have become such an everyday occurrence that we don’t even notice them … until they hit home.
Some of the cybercrime you don’t mind and even think it’s a good thing.
You know, it’s okay for your government to snoop in and around the other government’s systems because you want to know what they’re planning to do, and you want your country’s activities/secrets safe.
One of the best ways to ensure that is to poke in and around their systems to find out what they’re doing.
You know, the best defense is a good offense.
Whether it’s an offensive or defensive move, cybercrime is big business.
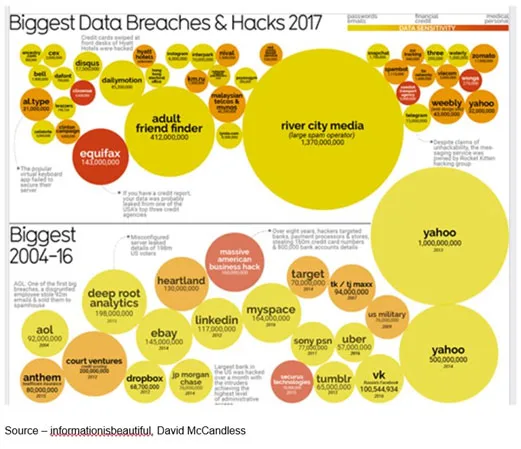
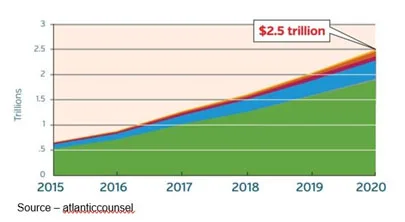
And it’s getting bigger!
The biggest problem is that the Internet (and later the Web) was designed and built to be open and fast to improve communications. That way, innovations could come faster, and things could be designed, built and introduced more quickly.
Back when Vint Cerf, Push Mohta and others rolled out the fledgling scientist/engineer communications service, it was all about techies sharing information.
Then, folks like Google, Alibaba, Facebook, Tencent, Amazon, Yahoo and hordes of others discovered it was a great way to encourage people to share their innermost thoughts and ideas in addition to buying stuff.
Then, others found they could keep you hooked by freeing you from your computer connection to use a tablet, smartphone, TV set, watch, game systems, refrigerators, cars, bathtubs, toilets, toys—heck, everything to stay in touch.
To do it, they built new software code and apps on top of old software code that was designed to do a job or thing … not to do something extraneous like security.
Governments still use these aging systems – IBM mainframes, Apple IIs, IBM PC XTs and clones like the ES EVM (ЕС ЭВМ), ES PEVM (ЕС ПЭВМ), M series, Minsk (Минск), Poisk (Поиск), Setun and others around the globe.

The good news for these agencies is that those systems and their software are so old no one can figure out how to write code that old to hack ‘em!
Today, every organization has some level of hacking capability – good hackers (white hats) and bad hackers (black hats).
It has gotten to the point where Brian Krebs (best known for Krebs on Security and his coverage of cybercrime, cybercriminals) and his security counterparts have a tough time keeping up.
All too often, they are tested by these hackers and whackers as well as cybercriminals; and they get to climb out from under the rubble and give us an eye witness report.
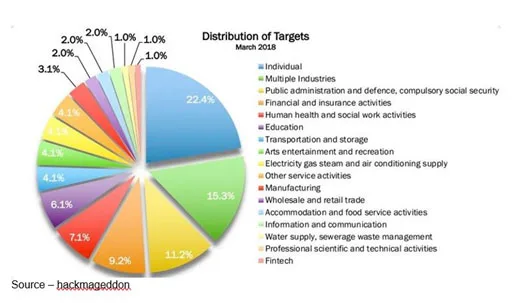
Cybersecurity experts all universally agree that there are only three types of companies:
- those that have been hacked
- those who don’t know they’ve been hacked
- those that will be hacked … shortly
There are a lot of user-proven techniques to get into an organization’s systems/networks.
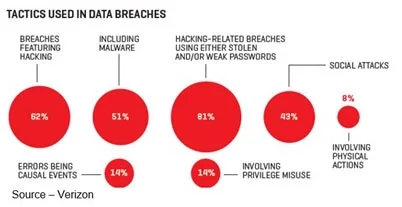
It’s pretty easy for a hacker to get into a firm’s system and grab the data they want. All it takes is a careless, greedy, dumb or sloppy user action.
You know:
- Helping a rich, dying old lady in England or Argentina spread her late husband’s wealth to the poor (with a decent fee for your services)
- An email from HR to fill out and return the attached form
- A bunch of photos from last weekend’s party your friend thought you’d like to see
- A notice from your bank on unusual activity in your account they need verified (click here)
- Secure passwords like 1234,6 or ABCDEF or the word “password”
Some are really creative.
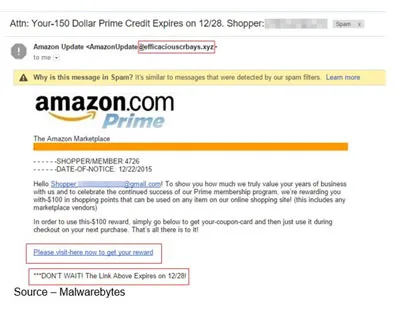
And when companies, governments get hacked, you get hacked!
Oh sure, you could avoid the possibility of being hacked by getting of the iNet and getting back to the basic things that really count.

Okay, maybe that’s a little drastic for you and your significant other.
But if your personal data has been put up for sale, there may be times you’ll seriously consider it … seriously.
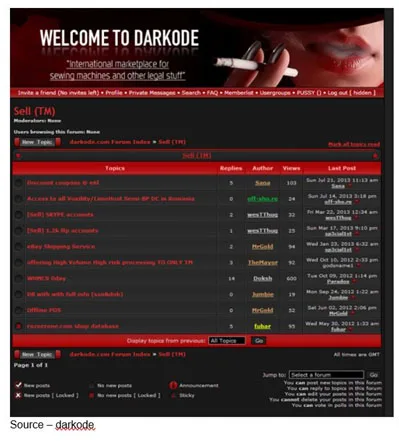
But if you decide packing up the old VW bus and heading for the back woods isn’t for you or just want to ensure you’re a little bit safe, you should:
- Check to see if you’ve been hit with a couple of different malware, security testing packages.
- Check haveibeenpwned.com to see if you dodged the bullet. It’s not a 100 percent guarantee, but it’s pretty good.
- See if you’ve been impacted and what info is at risk.
- Change questionable or shaky passwords.
- Don’t use a password for more than one location.
- Get a password manager – and use it (less than 12 percent of people do).
- For your sensitive info (credit cards, social security numbers, etc.) see if the hacked company offers one year of free monitoring service … and use it.
- Contact all of the credit monitoring services and consider a security freeze.
- Check to see if you’ve been pwned and credit services at least twice a year – threats can appear years from now.
- Change passwords at least every six months and keep your software password manager current.
- Consider hardware security options as well.

Why do all that work?
Well, according to a recent cybersecurity report, you cause 58 percent of all of your company’s breaches.
Don’t let cybersecurity people kid you, there’s no such thing as foolproof cybersecurity or privacy.
Trust us, there’s no shortage of fools who will consistently prove them wrong.
In addition, hackers who want to access a company’s business/customer data always seem to be one-two steps ahead of cybersecurity solutions.
That will be true even when we have AI-based cybersecurity solutions because:
- Really smart systems can’t figure out how to do stupid stuff
- It takes a lot of creativity to do bad things to other people
 As The Plague noted, “Let me explain the New World Order. Governments and corporations need people like you and me. We are Samurai… the Keyboard Cowboys… and all those other people who have no idea what’s going on are the cattle … Moooo.”
As The Plague noted, “Let me explain the New World Order. Governments and corporations need people like you and me. We are Samurai… the Keyboard Cowboys… and all those other people who have no idea what’s going on are the cattle … Moooo.”
Better hardware won’t help … better software won’t help.
Guess it’s up to us.
# # #