There’s No Business as Usual With Hackers, Cybercriminals and Cyberterrorists,
The Internet of things, a cashless society and cloud-based everything are all great dreams. But we are beginning to see that the dream can quickly turn into one helluva’ nightmare.
Up until the end of 2014, online attacks were directed at companies and institutions – private and public. Now it has gotten to the point that attacks on infrastructures, financial institutions and energy organizations are daily occurrences.
Security and law enforcement experts estimate that last year, as many as 80 percent of large companies have suffered a security breach.
The objective of these breaches were simple – steal intellectual property (IP), money or content (PIN numbers, email addresses, personal data) that had value to someone else or simply to test/prove their dark side software skills.
Hackers are very rarely caught.
Sony’s hack attack – compared to most last year – was relatively small in terms of fiscal damage (O.K., $100M in lost revenue isn’t small but …).
Target, Home Depot, JPMorgan, Adobe, eBay, Korea Credit Bureau and hundreds of others were larger because millions of credit cards and lots of corporate/personal data were stolen.
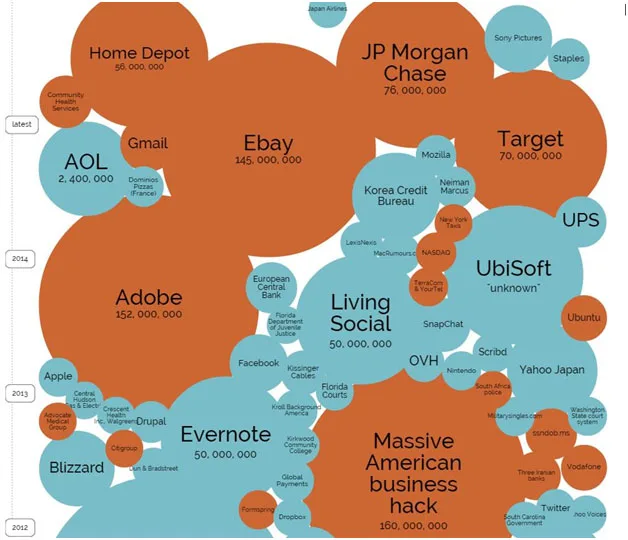
Big Race – The size and cost of hacks and attacks has grown significantly over the past year and shows little sign of shrinking. While Sony was far from being large in comparison to others, it exhibited a unique trend by being both aggressive and personal, exposing personal and corporate data.
Sony was different because it was all of that plus the humiliation/embarrassment of having individuals’ emails, stored ideas/thoughts released to the world.
The volume of cyber attacks – espionage and IP – will increase this year and will be more visible. There will also be an increase in “collateral damage.”
It will be a challenging time for IT personnel because they understand they have already been hacked and malware is already running on any number of organization systems … or it will be shortly.
By design and definition, networks and the Internet are not secure but they can be significantly improved by IT.
ISC-CERT (Industrial Control Systems Cyber Emergency Response Team) notes that there are a number of NTP (network time protocol) security holes that even individuals with limited skills can use for distributed denial of service (DDoS) attacks (basically shutting your organization, site down). The fixes have been around for years but only now are network administrators and equipment manufacturers beginning to implement them.
The bigger issue is that IT has to balance end-user productivity with security.
Management doesn’t worry about security as long as the work gets done quickly, properly.
Employees don’t care as long as the things they need are really available.
Accounting doesn’t care as long as everything comes in on budget.
Lawyers care about how much it costs in time and resources to achieve it.
Until now, IT has focused on meeting these requirements, pushing security implications into the background.
The problem with security is that everything is fine until it isn’t fine.
As a result, attackers have been able to move freely through the organization once the network/system walls have been breached.
It has been made even easier as organizations have rushed to embrace BYOD (bring your own device) so employees can access their content anytime, anywhere.
 Connected – Management initially liked the idea of BYOD with employees using their own mobile devices for work. It enabled people to be more productive and more available, but the devices have shown an ugly side as well. Apps are added with malware and they are often lost/stolen with vital corporate information on them.
Connected – Management initially liked the idea of BYOD with employees using their own mobile devices for work. It enabled people to be more productive and more available, but the devices have shown an ugly side as well. Apps are added with malware and they are often lost/stolen with vital corporate information on them.
Personal mobile devices, phones, tablets and laptops have created hundreds/thousands of network entry points that put personal information and confidential data at risk.
Few of us “normal” folks really understand or practice safe computing.
At its best, information is protected with a username and simplistic password.
IT practices such as multi-factor authentication, special privilege mandates to access content, eliminating end-user admin permission, mandatory watermarking of documents/content for viewing printing, copying and forwarding, as well as active logging of system activities won’t eliminate network/system penetration completely, but it will make it more difficult.
This year, we’ll see a rush of VC investments in new automated security solution firms that will promise nearly penetration-proof solutions for organizations.
The problem in most organizations, the areas for potential attack are so vast that motivated hackers will always find a way in, usually courtesy of an innocent insider who fell for a spear-phishing campaign and opened the door.

Then they’ll hear Freddy Krueger say, ‘We got special work to do here, you and me.”
Once the attackers establish their beachhead, it usually becomes a simple matter of moving throughout the network and gathering information.
Hacking is a race between enterprise security and hackers. Unfortunately, the hackers are pulling ahead.
Until organizations do a better job training staff — especially individuals with sensitive data access, executives and their key staff — the number of attacks and losses will only grow.
The FBI stated that 90 percent of companies could not have defended against the Sony hack, which means organizations have a lot of work ahead of them.
But it isn’t impossible if businesses and institutions take a proactive position:
- Make security everyone’s responsibility: Education, awareness and personal responsibility are powerful deterrents.
- Don’t rely on technology: Tools are nice but reducing the amount of sensitive, private data stored in the insecure Cloud, eliminating insecure suppliers and restricting information access is a lot more effective and economic.
- Manage mobil devices: While devices can be hacked, the major issue is their being lost or stolen. While initially more costly, many organizations are returning to a COPE (corporate owned, personally enabled) program where devices have secure areas for work-related materials/information and personal areas.
- Develop and maintain a risk-aware environment: Information security needs to become an integral part of every aspect of the business so it is viewed as a normal business process, not a business blocker to be circumvented.
- Provide top-down support: If organizational data, information and content are everyone’s responsibility, with the CEO leading by example, it is more readily made a part of everyone’s daily activities.
Hacking tools have been around for some time and are becoming increasingly sophisticated and malicious.
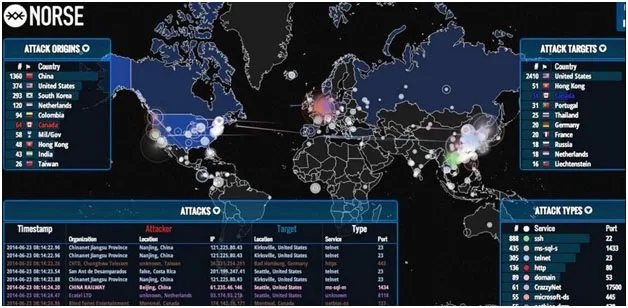 Realtime Strikes – The map may look like a pinball game with lights glittering here and there, but it’s really the tracking of IP addresses and the attacks against them. The volume of activity is steadily increasing.
Realtime Strikes – The map may look like a pinball game with lights glittering here and there, but it’s really the tracking of IP addresses and the attacks against them. The volume of activity is steadily increasing.
With their growing complexity and functionality, they can inflict damage on national and multi-national organizations that can extend beyond cybercrime to include cyber-bullying and cyber-terrorism.
It’s all empowered by our addiction to, and reliance on, technology.
It can only be avoided by getting completely off the grid, using cash, dispensing with credit cards, never browsing the Internet, using pre-paid cell phones, giving up your driver’s license and every other government-related document/service.
It can only be ended by a complete revision of our technological infrastructure.
Since none of these scenarios is likely, organizations and individuals have to come to grips with the fact that individuals are developing and releasing malware that can wipe data from their systems, rendering it beyond recovery. They have no choice but to improve their cybersecurity vigilance.
Ultimately, organizations and individuals will learn to live with the constant threat, knowing that some days the good guys will be ahead and some days the bad guys will be ahead.
Being aware, prepared and practicing sound computing/security processes and procedures can level the playing field, improving your odds.
 Organizations and individuals will learn to take Lisa’s advice, “Fight him. You are not afraid of him!”
Organizations and individuals will learn to take Lisa’s advice, “Fight him. You are not afraid of him!”
Increasingly, we’ll be as proactive as Ken Walsh, “What that boy needs is a good god damn kick in the butt, that’s what he needs!”
# # #